In this blog, Roberta Faux outlines the cryptographic events which led to NIST's Post-Quantum Cryptography competition and those after which are shaping the cyber landscape of today.
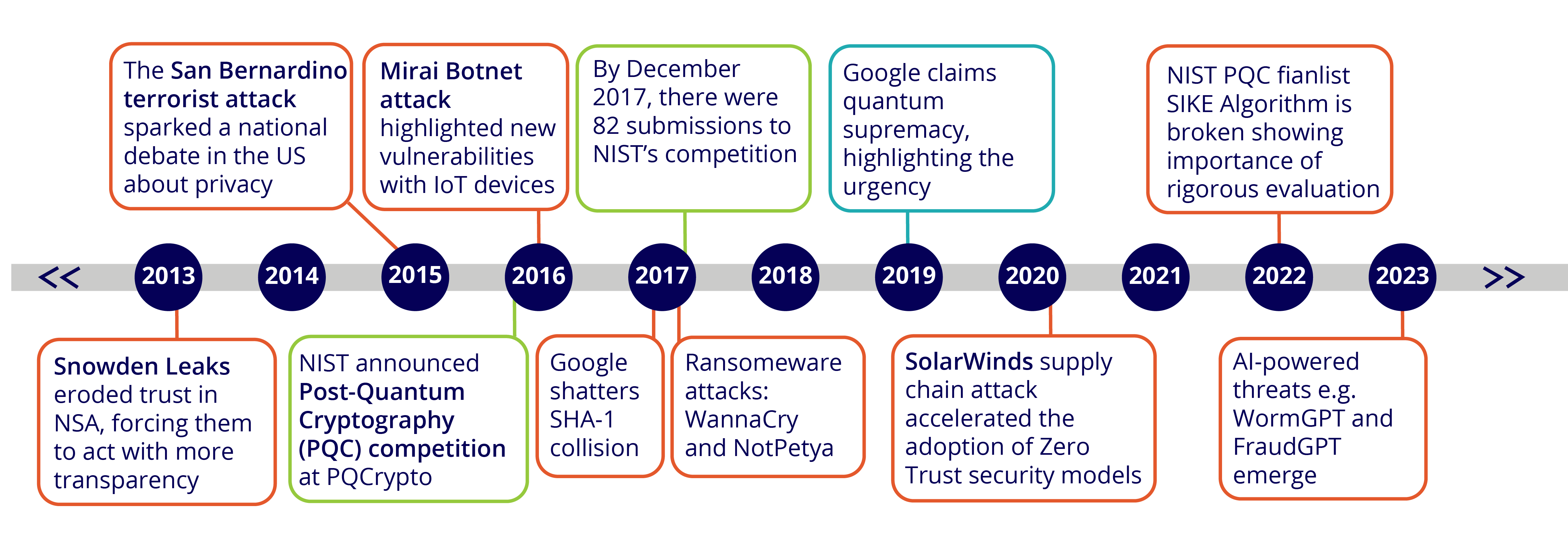
The year 2016 was a pivotal moment for digital security. In February, at the PQCrypto 2016 conference in Fukuoka, Japan, Dr. Dustin Moody of the National Institute of Standards and Technology (NIST) made the landmark announcement regarding an upcoming Post-Quantum Cryptography (PQC) competition.
The announcement was a formal, direct declaration of a new reality in cryptography. It was not so much of a surprise, after years of growing concern within the academic and intelligence communities. The message was clear: the cryptographic landscape was on the brink of a revolution.
In a field where theoretical discussions are common, this announcement was a decisive call to action with the presentation titled "Post-Quantum Cryptography: NIST's Plan for the Future.” It outlined a structured plan and timeline for a global, multi-year competition, signaling to the world's cryptographers that it was time to move from theory to practical implementation. This moment marked a fundamental shift from discussing the "what-if" of quantum threats to actively building a defense against them.
Recognizing the looming threat of quantum computers, including concerns from NSA, NIST launched a competition to develop new, quantum-resistant public key cryptographic standards. Cryptographers from all over the world sent proposed algorithms to NIST. By November 30, 2017, there were 82 submissions, 69 of which were deemed complete and proper. This began the first round of the post-quantum cryptography evaluations.
What no one fully anticipated was the dramatic and unpredictable evolution of the cybersecurity landscape that would unfold over the following decade. While NIST's PQC competition was underway, the world was being reshaped by a series of events that fundamentally changed how we use and secure technology.
A Decade of Unforeseen Challenges
The Shadow of Snowden
Even before the competition began, the revelations from the Snowden leaks significantly complicated NIST’s efforts due to the erosion of public and academic trust in the agency. The leaks exposed that the NSA had allegedly actively worked to weaken cryptographic standards and protocols, including its role in introducing a flawed random number generator, known as Dual EC_DRBG – a NIST standard! This history made many in the cryptographic community skeptical of NIST's motives and oversight, prompting concerns that a new set of PQC standards might be similarly compromised. The distrust forced NIST to operate with greater transparency and under far more scrutiny than it had in the past. This forever changed the public perception and the collaborative dynamics of the standards-setting process.
Trust and Privacy Debates
The 2015 San Bernardino terrorist attack sparked a national debate in the United States about privacy, security, and the role of technology companies in law enforcement investigations. The FBI's attempts to force Apple to unlock the iPhone of one of the shooters brought the issue of encrypted data and its accessibility by law enforcement to the forefront. This event forced a public reckoning with the very nature of trust in our digital systems and highlighted the competing interests of technology companies, which prioritize user privacy, and law enforcement, which seeks to prevent future attacks. This debate over privacy, security, and government access to private data made it clear that public and governmental scrutiny would be a core component of any future cryptographic standard, including the NIST Post-Quantum Cryptography (PQC) competition.
Cryptanalysis
Just over a year after the PQC competition was launched, Google announced it had successfully performed the first SHA-1 collision attack. This attack came faster than many predicted and demonstrated that the security of this widely used, though deprecated, algorithm, long considered secure enough for many applications, was no longer theoretical. This real-world example of how a once-trusted algorithm could be broken indicated that cryptanalysis was advancing faster than many had anticipated, reinforcing the need for a rigorous, transparent, and proactive process to develop the next generation of cryptographic standards.
IoT
The ubiquity of the Internet of Things (IoT) exploded in scale, creating new cyber vulnerabilities at an unprecedented level. This also presented a challenge that the NIST PQC competition, which was focused on the threat of quantum computers, had not fully anticipated. The Mirai Botnet, for example, turned everyday IoT devices into a cyber weapon. In addition, malware such as VPNFilter began to specifically exploit IoT devices for malicious purposes. The danger was made clear by an attack that altered chemical levels at a Florida water treatment facility. These events, along with the issue of "abandonware IoT" with long lifespans and no update plans, showed that the digital landscape was becoming more sophisticated, complex, and faster than originally assumed. This underscored that the need for cryptographic standards to be resilient not only to quantum computers, but to a vast, complex, and insecure IoT-enabled world
Ransomware
Massive global ransomware attacks like WannaCry and NotPetya marked a terrifying new chapter in cyber warfare. These incidents demonstrated a new level of sophistication and disruption, as they were able to spread rapidly and indiscriminately across the globe. These attacks were often made possible by new innovations that enabled them to be weaponized for widespread chaos. The success of these global events spawned a surge in ransomware attacks against schools, cities, and hospitals, which became a terrifying reality for many. This highlighted how cryptography and malware were advancing faster than many had predicted, revealing the insecurity of our dynamic digital world.
Supply Chain Attacks
The SolarWinds supply chain attack was a landmark event that profoundly accelerated the adoption of Zero Trust security models. Malicious actors were able to compromise SolarWinds' software and embed malware into a trusted update, which was then distributed to thousands of governments and corporate customers. This attack demonstrated that even the most trusted vendors and software could not be implicitly relied upon. It shattered the traditional security model, which focused on strong perimeter defenses and assumed everything inside the network was safe. This pivoted the industry to the Zero Trust principle: "never trust, always verify" - a mandatory strategy for modern cybersecurity.
Quantum Supremacy
The first claims of quantum supremacy in 2019 came sooner than expected. Google gave a powerful and urgent wake-up call for the cryptographic community during the momentum to the NIST PQC effort. While the theoretical threat of quantum computers had been the motivation for the competition, these claims provided the first tangible evidence that a powerful quantum computer was not a distant fantasy, but an emerging reality. This set the clock on our existing public-key infrastructure, forcing governments and private sectors to accelerate their transition to impending quantum-resistant standards.
More Cryptanalysis
In the final stages of the NIST PQC Standardization Process, one notable algorithm, SIKE (Supersingular Isogeny Key Encapsulation), was broken shortly before the final standards were released in 2024. SIKE, a fourth-round candidate for key establishment, was compromised in August 2022 by researchers Wouter Castryck and Thomas Decru using a classical computer, exploiting vulnerabilities in its structure. This breakthrough demonstrated that SIKE was not quantum-resistant, leading to its exclusion from NIST’s finalized standards. The incident underscored the importance of NIST’s rigorous, multi-round evaluation process, as it allowed the cryptographic community to identify weaknesses before standardization, ensuring only robust algorithms were selected to protect against future quantum threats.
Gen AI
The dramatic rise of Generative AI and its applications in cybersecurity has become a significant and unforeseen challenge. While NIST was focused on the quantum threat, powerful new tools emerged that would both enhance and threaten digital security. AI-powered threats such as deepfake phishing and the emergence of custom Large Language Models (LLMs) like WormGPT and FraudGPT have allowed malicious actors to craft sophisticated malware and phishing campaigns at an unprecedented scale. Furthermore, the algorithms being developed for the PQC competition are now facing new forms of cryptanalysis, as researchers are beginning to use AI and machine learning to augment traditional methods for discovering weaknesses and side-channel vulnerabilities. This reality demonstrates that the digital landscape is more complex and insecure than ever before, and that the next generation of cryptography must be resilient to both quantum computers and the unforeseen advancements in AI.
Conclusion: A Need for a New Mindset
The NIST PQC competition began with a focus on a single, albeit massive, threat: the quantum computer. It was an essential and forward-looking effort. However, in hindsight the highly dynamic digital world we inhabit today could not have been predicted. The NIST process did not fully anticipate the rise of IoT, the new attack vectors, or the speed at which malware would evolve.
Today, the digital landscape is defined by its complexity and insecurity. We need solutions that are dynamic, scalable, agile, cost-effective, and lightweight. The past decade has shown us that securing the future requires more than just new algorithms; it requires a new mindset - one of cryptographic agility and constant innovation to stay ahead of an ever-changing threat landscape.
27 October 2025
Roberta Faux, US Head of Cryptography, Arqit

